Reverse engineering an APK file is a process that involves decompiling and analyzing the code and resources within an Android application package (APK). This allows developers to examine the inner workings of an app, potentially to understand its functionality, identify vulnerabilities, or even modify its behavior. It’s a topic that sparks curiosity and raises questions about ethical implications and practical applications.
Understanding APK Reverse Engineering
So, can you actually reverse engineer an APK file? The short answer is yes, but it’s more complex than simply clicking a button. Reverse engineering requires specific tools and a certain level of technical expertise. The level of difficulty depends on the complexity of the app and the obfuscation techniques employed by the developers. Obfuscation is a method used to make the code harder to understand, essentially acting as a deterrent against reverse engineering.
Why Reverse Engineer an APK?
There are several reasons why someone might want to reverse engineer an APK file. Security researchers might do it to identify vulnerabilities and improve app security. Developers can use it to learn from other apps, understand how specific features are implemented, or even troubleshoot compatibility issues. apk sdk analyzer is a tool helpful in such cases. In some cases, modders might reverse engineer an app to modify its functionality, create custom themes, or unlock premium features. However, it’s important to be mindful of the ethical and legal implications, as modifying and distributing copyrighted material without permission is illegal.
Tools for Reverse Engineering
Several tools are available for reverse engineering APK files. Some popular choices include:
- Apktool: This tool is commonly used for decompiling and rebuilding APK files. It allows access to the resources and code, making it easier to analyze the app’s structure and functionality.
- dex2jar: This tool converts the Dalvik Executable (.dex) files within the APK into Java Archive (.jar) files, which can then be explored using Java decompilers.
- JD-GUI: A Java decompiler that helps make sense of the decompiled .jar files, presenting the code in a more readable format. This allows for easier analysis of the app’s logic. You can even consider tools like apk studio.
Legal and Ethical Considerations
While reverse engineering itself isn’t always illegal, it’s crucial to be aware of the legal and ethical implications. Reverse engineering copyrighted apps for commercial purposes or to distribute modified versions without permission is illegal. Always respect intellectual property rights and use these techniques responsibly. Think about the issues you might encounter, such as a build release apk error. It’s also important to avoid using reverse engineering for malicious purposes like creating malware or stealing sensitive information. If you’re interested in building an APK using Android Studio, that’s a more legitimate path to take.
Is Reverse Engineering Difficult?
The difficulty of reverse engineering an APK file can vary. Simple apps with little to no obfuscation are generally easier to analyze. However, complex apps employing advanced obfuscation techniques can be significantly more challenging.
How to Protect Your APK
Developers can employ several techniques to protect their APK files from reverse engineering. Obfuscation, as mentioned earlier, is a common practice. Other methods include using encryption to protect sensitive data within the app and implementing checks to detect tampering or debugging attempts. Even simple tasks like editing APK files on your phone can be relevant to understand the structure and potential vulnerabilities.
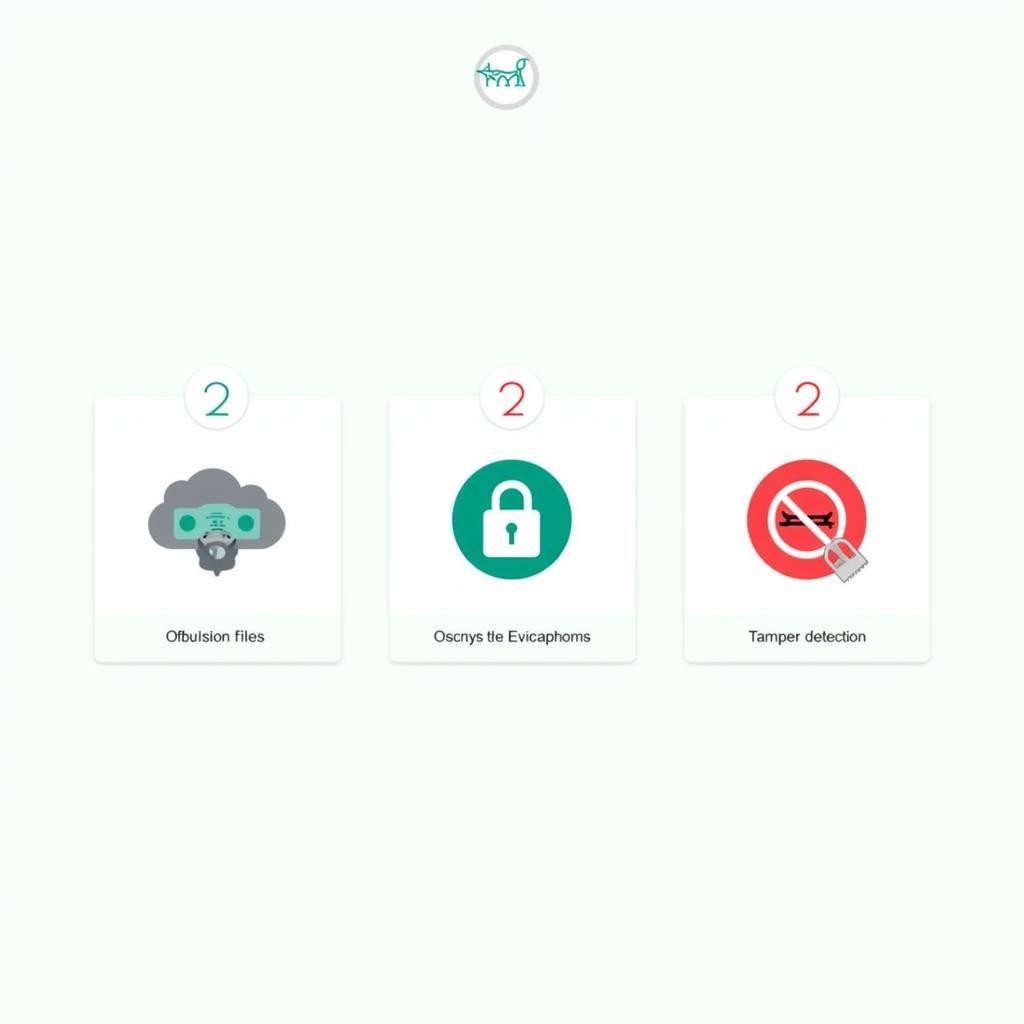 APK Protection Techniques
APK Protection Techniques
Conclusion
Reverse engineering an APK file is possible with the right tools and knowledge. While it can be used for legitimate purposes like security research and learning, it’s crucial to be mindful of the legal and ethical boundaries. Remember, responsible use of these techniques is essential to avoid infringing on intellectual property rights and causing harm. If you are looking into reverse engineering, ensure you understand the potential consequences and act responsibly.
FAQ
- Is it legal to reverse engineer an APK? Reverse engineering itself is not always illegal, but using it to infringe on copyrights is.
- What are the common tools for reverse engineering? Apktool, dex2jar, and JD-GUI are frequently used tools.
- Why do developers obfuscate their code? Obfuscation makes code harder to understand, deterring reverse engineering.
- How can I protect my APK from reverse engineering? Obfuscation, encryption, and tamper detection are some protective measures.
- What is the purpose of reverse engineering? It can be used for security research, learning, or even modifying app behavior.
- Is reverse engineering difficult? The difficulty varies depending on the app’s complexity and obfuscation techniques.
- Where can I learn more about reverse engineering? Online resources, tutorials, and communities can provide valuable information.
For support, please contact Phone Number: 0977693168, Email: [email protected] or visit us at 219 Đồng Đăng, Việt Hưng, Hạ Long, Quảng Ninh 200000, Vietnam. We have a 24/7 customer support team.