Extracting code from an APK file, often referred to as “decompiling”, can be a valuable skill for developers, security researchers, and curious users alike. This process allows you to inspect the inner workings of an Android application, potentially revealing hidden features, vulnerabilities, or simply understanding how a particular app functions.
Understanding APK Files and Decompilation
Before diving into the how-to, let’s briefly understand what an APK file is. An APK (Android Package Kit) file is the packaged format used to distribute and install applications on Android devices. It contains all the essential components of an app, including code (in the form of Dalvik bytecode), resources, manifest file, and certificates. Decompilation is essentially the reverse engineering process of transforming this bytecode back into a more readable format, such as Java code. While you won’t retrieve the original source code exactly, the decompiled code provides a close approximation, allowing for analysis and modification. This can be particularly useful for understanding how an app implements specific features, identifying potential security flaws, or even adapting functionalities for your own projects.
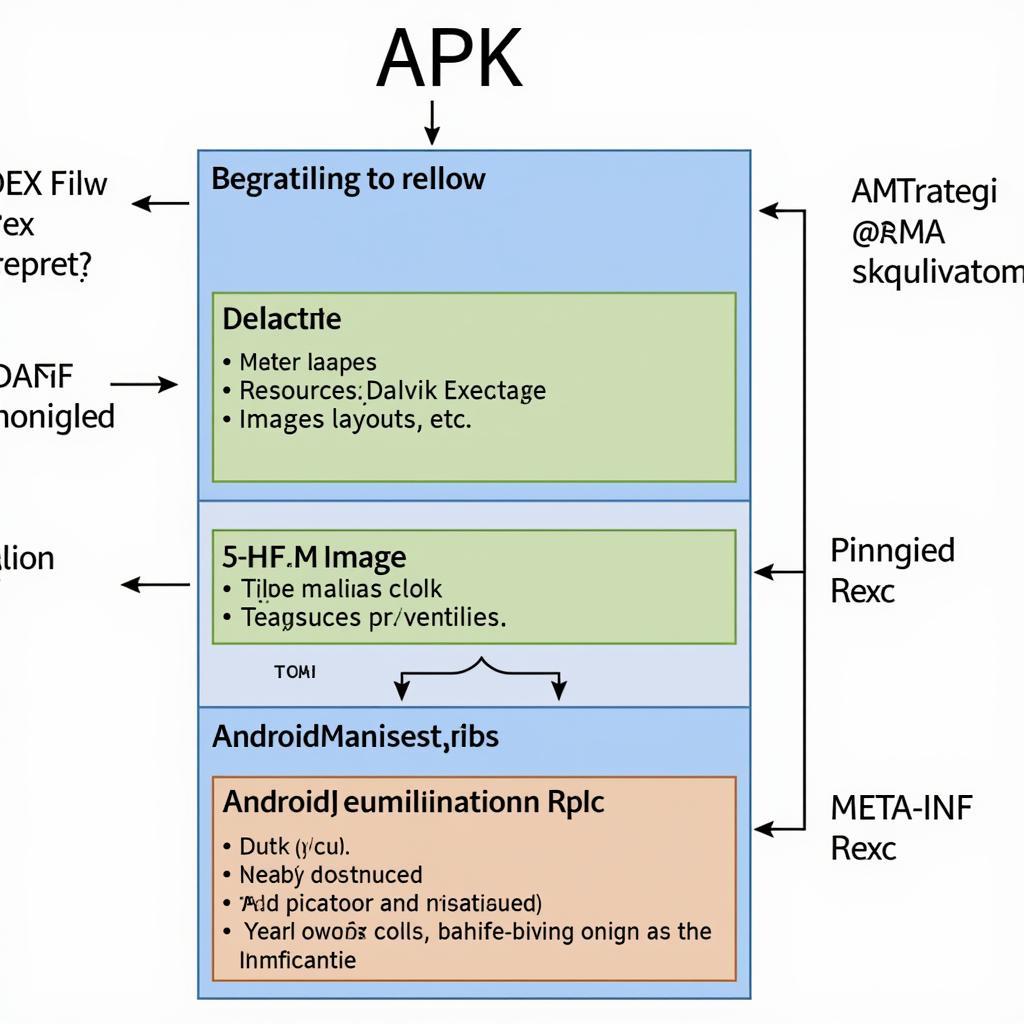 APK File Structure and Components
APK File Structure and Components
Tools for Extracting Code from APK Files
Several tools are available to help extract code from APK files. Some of the popular options include:
-
JADX: JADX is a powerful command-line and GUI tool that decompiles Dalvik bytecode into Java source code. It’s known for its accuracy and ease of use, making it a favorite among developers. apk focus full
-
dex2jar: dex2jar converts the DEX files within an APK to a JAR file, which can then be opened and inspected using standard Java decompilers like JD-GUI. can apk
-
APKtool: APKtool is primarily used for decoding resources and rebuilding APKs, but it can also be used to disassemble the code into a somewhat readable format called Smali. barcode knight full apk
Step-by-Step Guide Using JADX
Here’s a simple guide to extracting code using JADX:
-
Download and Install JADX: Download the latest version of JADX from the official website. It’s available for Windows, macOS, and Linux.
-
Open the APK in JADX: Once installed, launch JADX and open your target APK file.
-
Explore the Decompiled Code: JADX will decompile the APK and present the Java code in a navigable tree structure. You can browse through the different classes and methods to analyze the app’s functionality.
Ethical Considerations
While extracting code from APKs can be beneficial for learning and research, it’s important to consider ethical implications. Decompiling copyrighted applications without permission can be illegal. Always ensure you have the right to analyze an app’s code, especially if you plan to modify or redistribute it.
Conclusion: Unlocking the Secrets Within APKs
Learning how to extract code from an APK file can be a valuable asset for anyone working with Android applications. From understanding app behavior to identifying security vulnerabilities, the ability to decompile APKs opens up a world of possibilities. Remember to use this knowledge responsibly and ethically, respecting the rights of app developers. Are you interested in exploring more about APK modifications? Check out build apk use eclipse and chạy file apk mod.
FAQ
-
Is decompiling an APK legal? It depends on the specific app and your intended use. Decompiling copyrighted apps without permission can be illegal.
-
Can I retrieve the exact original source code? No, decompilation provides a close approximation but not the original source code.
-
What is the best tool for extracting code? JADX is a popular choice due to its accuracy and ease of use.
-
Can I modify the decompiled code? Yes, but be mindful of legal and ethical considerations.
-
What is Smali? Smali is an assembly language for the Dalvik virtual machine.
-
How can I learn more about Android app development? There are numerous online resources and courses available.
-
What are some common use cases for decompiling APKs? Security analysis, understanding app functionality, and learning from others’ code.
Common Scenarios and Questions
Scenario: You encounter a bug in an app and want to understand its root cause.
Question: How can I inspect the app’s code to identify the source of the error?
Scenario: You’re curious about how a specific feature in an app is implemented.
Question: Can I decompile the APK to see the code behind that feature?
Scenario: You suspect an app might have security vulnerabilities.
Question: How can I analyze the code for potential security flaws?
Further Exploration
You might also be interested in learning about:
- Reverse engineering Android apps
- Android security best practices
- App development frameworks
For any further assistance, please don’t hesitate to contact us: Phone: 0977693168, Email: [email protected] or visit our office at 219 Đồng Đăng, Việt Hưng, Hạ Long, Quảng Ninh 200000, Vietnam. We have a 24/7 customer support team ready to help.