Decompiling Android APK files into Java source code is a common task for developers and security researchers. It allows them to analyze an app’s inner workings, understand its logic, and potentially identify vulnerabilities. One of the most popular tools for this purpose is Apktool. This guide will delve into the process of using Apktool to decompile APK files into Java, discussing its features, advantages, and limitations.
Understanding APK Decompilation
Before we dive into the technicalities of using Apktool, it’s crucial to understand what APK decompilation entails and its implications.
What is an APK file?
An APK (Android Package Kit) file is the package format used to distribute and install applications on the Android operating system. It’s essentially a ZIP archive containing all the necessary files for an app to function correctly, including:
- Classes.dex: This file holds the application’s compiled code in Dalvik Executable format (DEX), optimized for Android runtime.
- AndroidManifest.xml: This XML file contains essential information about the application, such as its package name, permissions, and components.
- Resources: This folder contains various resources like images, layouts, and strings used by the application.
- META-INF: This folder often contains the application’s signature and other metadata.
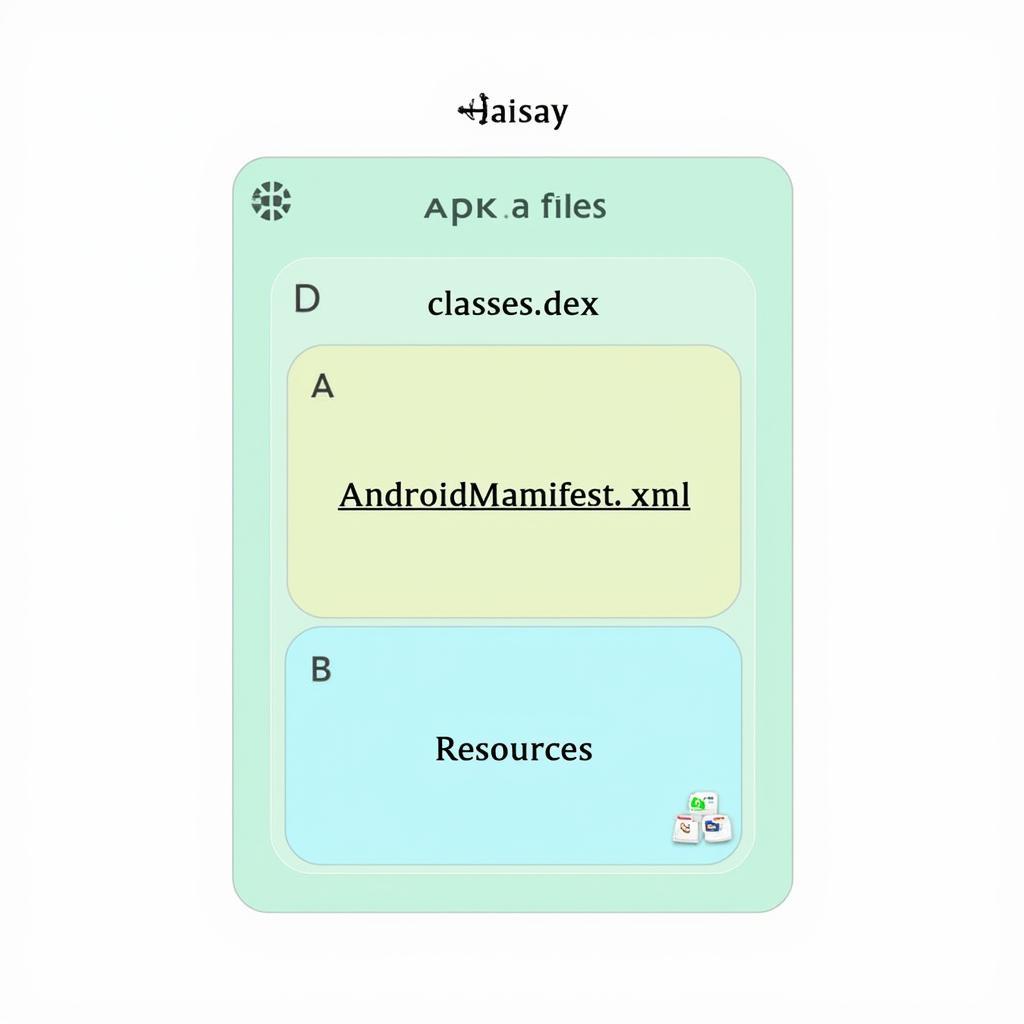 apk file structure
apk file structure
What is Decompilation?
Decompilation is the process of reversing the compilation process, attempting to reconstruct high-level source code from the compiled executable. In the context of APK files, it involves converting the DEX bytecode within the “classes.dex” file back into somewhat readable Java code.
Important Note: Decompilation won’t produce the original source code. It generates a close approximation that might differ in variable names, comments, and code structure.
Why Decompile APKs?
Decompiling APKs can be valuable for various reasons, including:
- Security Analysis: Researchers and ethical hackers use decompilation to uncover potential vulnerabilities in applications.
- App Reversing: Understanding how an existing app works can be beneficial for educational purposes or developing similar functionalities.
- Bug Fixing & Modding: Some developers decompile APKs to fix bugs in open-source projects or create modifications for existing applications.
Ethical Considerations: While APK decompilation is legal for specific purposes like security research, it’s crucial to respect intellectual property rights and avoid using it for malicious activities like creating unauthorized copies or distributing modified versions without permission.
Apktool: The Go-To Tool for Decompilation
Apktool is an open-source command-line tool specifically designed for reverse engineering Android APK files. Unlike other tools that only target the DEX bytecode, Apktool aims to decode resources to their nearest possible original form and rebuild modified APKs from them.
Key Features of Apktool:
- Decompiling Resources: Apktool excels at decoding binary resources like layouts, images, and XML files into a human-readable format.
- Rebuilding APKs: It allows modifications to the decompiled resources and code, enabling you to rebuild a functional APK.
- Smali Debugging: Apktool uses Smali, an assembly-like language for Android, to represent the decompiled code, which you can modify and debug.
- Framework Support: It supports various Android frameworks, ensuring compatibility with a wide range of APKs.
 Apktool decompilation process
Apktool decompilation process
Getting Started with Apktool
Prerequisites:
- Java Development Kit (JDK): Apktool requires JDK installed on your system.
- Apktool Jar File: Download the latest Apktool JAR file from the official website.
- Command Prompt/Terminal: You’ll need a command-line interface to execute Apktool commands.
Decompiling an APK:
-
Open your command prompt or terminal and navigate to the directory where you saved the Apktool JAR file and the APK you want to decompile.
-
Execute the following command, replacing “app.apk” with your APK file name:
java -jar apktool.jar d app.apk -
Apktool will decompile the APK and create a new folder with the same name as the APK, containing the decompiled resources and Smali code.
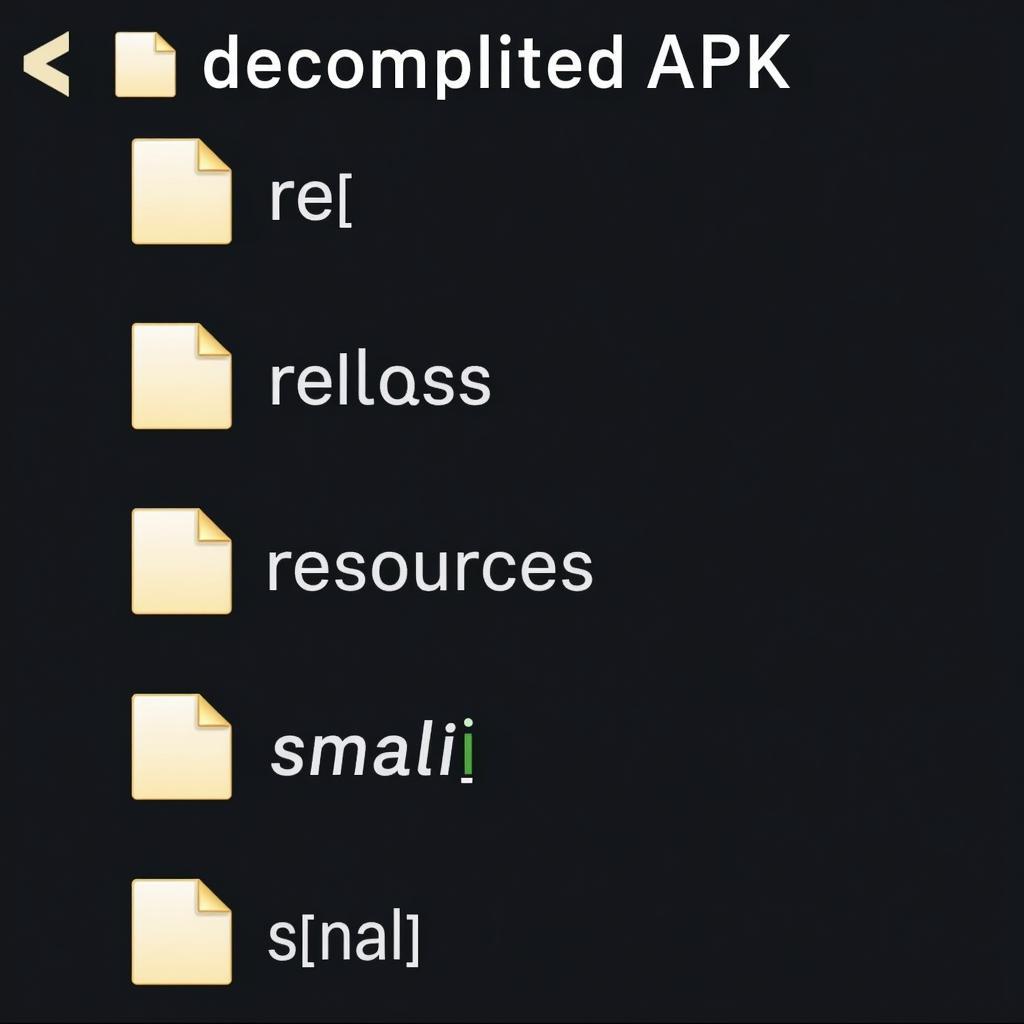 Decompiled APK folder structure
Decompiled APK folder structure
Exploring the Decompiled Output
After decompiling, you’ll find several folders and files within the newly created directory.
- res/: This folder contains the decompiled resources, including layouts, images, and values.
- smali/: This folder holds the decompiled Smali code representing the app’s logic.
- AndroidManifest.xml: This file contains the decompiled Android manifest, now in a readable XML format.
Working with Smali Code
Smali code might seem daunting initially, but it’s essential to understand its structure to modify the application’s behavior. Each Smali file corresponds to a Java class, and you can use a text editor to view and edit them.
Rebuilding the APK
After making changes to the decompiled resources or Smali code, you can rebuild the APK using Apktool:
java -jar apktool.jar b app-folderThis command will rebuild the APK using the files in the “app-folder” directory (replace with your folder name). The rebuilt APK will be located in the “app-folder/dist” directory.
Conclusion
Apktool is an invaluable tool for decompiling and analyzing Android APK files. It provides insights into an app’s inner workings, making it a powerful tool for security researchers, developers, and anyone curious about understanding Android applications better. Remember to use this knowledge ethically and responsibly. If you’re looking to delve deeper into Android app development, explore our other resources on apk decompile command, apk tool latest, and apktool unpack apk.