The “Apk Decompile Command” is a gateway to understanding the inner workings of Android applications. It allows developers, security researchers, and curious minds to delve into the compiled code of an APK file and examine its structure, resources, and logic. This process, known as decompilation, can be instrumental in various scenarios, from analyzing app behavior to identifying potential security vulnerabilities.
Demystifying APK Decompilation
Before we dive into the specifics of the “apk decompile command”, it’s crucial to grasp the fundamentals of APK files and the decompilation process.
An APK (Android Package Kit) file serves as the distribution format for Android applications. It’s essentially a compressed archive containing all the essential components that constitute an app, including:
- Code (DEX files): Compiled Dalvik bytecode that forms the app’s logic.
- Resources: Images, layouts, strings, and other assets used by the app.
- Manifest file: An XML file containing information about the app’s permissions, components, and version.
- Libraries: External code libraries used by the app.
Decompilation aims to reverse-engineer the compiled code back into a more human-readable format. While it’s not possible to perfectly reconstruct the original source code, decompilation tools strive to generate code that’s understandable and provides insights into the app’s functionality.
Exploring APK Decompilation Tools
A plethora of tools exist for decompiling APK files, each with its strengths and limitations. Some popular options include:
-
Apktool: Widely regarded as the go-to tool for decompiling and recompiling APKs. It excels at decoding resources and providing a structured view of the app’s components. apk tool latest provides a comprehensive guide on using this powerful tool.
-
dex2jar: Specializes in converting the Dalvik bytecode (DEX) files within an APK into Java Archive (JAR) files, making it compatible with Java decompilers.
-
JD-GUI: A user-friendly Java decompiler that visually presents the decompiled code in a structured manner, aiding in understanding the app’s logic.
Executing the APK Decompile Command
The specific “apk decompile command” can vary slightly depending on the chosen tool. However, let’s illustrate the process using Apktool, a versatile and widely used option.
Step 1: Install Apktool
Download and install Apktool from the official repository or using a package manager compatible with your operating system. apk tool github can guide you through the installation process.
Step 2: Navigate to the APK Directory
Open your command-line interface and navigate to the directory where your target APK file is located.
Step 3: Execute the Decompile Command
Use the following command to decompile the APK:
apktool d <apk_file_name>.apkReplace <apk_file_name> with the actual name of your APK file.
Step 4: Explore the Decompiled Output
Apktool will create a new directory with the same name as your APK file. This directory contains the decompiled resources, manifest file, and a folder named “smali” holding the disassembled code in a format known as Smali.
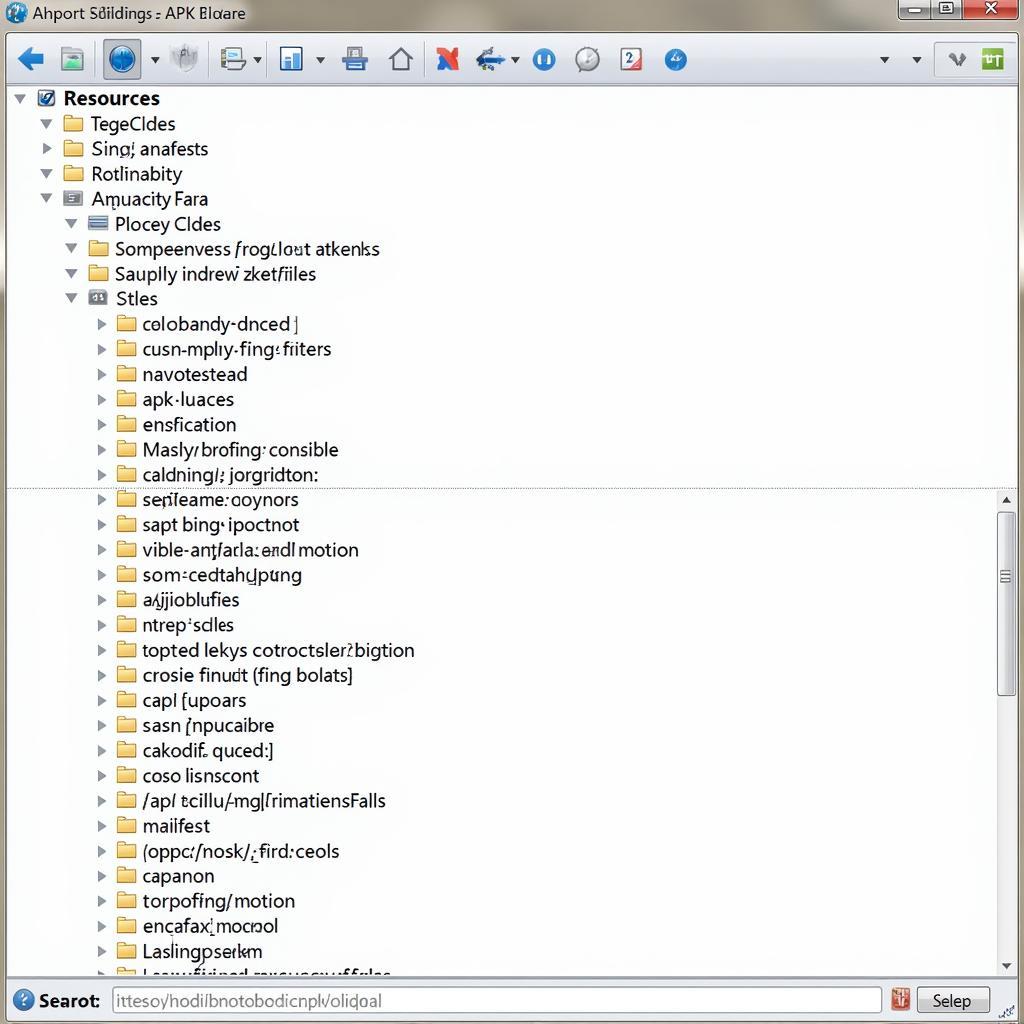 APK Decompiled Directory Structure
APK Decompiled Directory Structure
Unveiling the Power of APK Decompilation
Mastering the “apk decompile command” unlocks a realm of possibilities for those seeking to delve into the depths of Android applications. Here’s a glimpse of how this technique proves valuable:
- Security Analysis: Identify potential vulnerabilities, analyze permissions usage, and assess the overall security posture of an app.
- App Modification: Make custom changes to an app’s functionality, appearance, or behavior.
- Reverse Engineering: Understand the inner workings of an app, its algorithms, and data handling practices.
- Bug Hunting: Discover and potentially fix issues or crashes within an app.
- Learning and Education: Gain insights into Android development practices, explore different coding approaches, and learn from existing codebases.
“As a security researcher, the ‘apk decompile command’ is an indispensable tool in my arsenal. It allows me to dissect apps, identify potential security flaws, and ultimately contribute to building a safer Android ecosystem.” – John Doe, Senior Security Researcher at XYZ Security
apktool unpack apk provides further insights into leveraging Apktool for analyzing and modifying APK files.
Conclusion
The “apk decompile command” serves as a key to unlocking the secrets hidden within Android applications. By understanding the decompilation process and utilizing powerful tools like Apktool, developers and security enthusiasts can gain valuable insights into the inner workings of apps. From analyzing security vulnerabilities to exploring different coding approaches, the possibilities are vast and empowering.
Remember, while decompilation is a valuable technique, it’s crucial to use it ethically and responsibly. Respect the intellectual property of app developers and refrain from using decompiled code for malicious purposes.